bxm's IT Story
프로젝트 본문

## VTP ##
공통]
conf t
no ip domain lookup
line c 0
logg sy
exec-timeout 0
exit
line vty 0 4
pass cisco
exit
vtp mo tr
end
wr
DSW1, DSW2, R4]
conf t
ip routing
end
wr
ASW1, ASW2, S_SW]
conf t
no ip routing
end
wr
## VLAN ##
## INSIDE (DSW1,2-VLAN 10,20,30,40,50 // ASW1-VLAN 10,20 // ASW2-VLAN 30,40)
DSW1, DSW2]
conf t
vlan 10
exit
vlan 20
exit
vlan 30
exit
vlan 40
end
wr
ASW1]
conf t
vlan 10
exit
vlan 20
end
wr
ASW2]
conf t
vlan 30
exit
vlan 40
end
wr
## DMZ (실제로는 안해도 된다. 다이렉트로 연결된 것이 ASA밖에 없기 때문에)
S_SW]
vlan 50
end
wr
## OUTSIDE
R4]
conf t
vlan 70
end
wr
## Access & bpduguard ##
ASW1]
conf t
int f1/1
sw mo ac
sw ac vlan 10
spanning-tree portfast
exit
int f1/2
sw mo ac
sw ac vlan 20
spanning-tree portfast
exit
spanning-tree portfast bpduguard
end
wr
## f1/1과 f1/2 쪽으로 bpdu를 보내지 않겠다 라는 뜻임.
ASW2]
conf t
int f1/3
sw mo ac
sw ac vlan 30
spanning-tree portfast
exit
int f1/4
sw mo ac
sw ac vlan 40
spanning-tree portfast
exit
spanning-tree portfast bpduguard
end
wr
S_SW]
conf t
int range f1/1 - 4
sw mo ac
sw ac vlan 50
spanning-tree portfast
exit
spanning-tree portfast bpduguard
end
wr
R4]
conf t
int range f1/9 - 10
sw mo ac
sw ac vlan 70
spanning-tree portfast
exit
spanning-tree portfast bpduguard
end
wr

## Trunking ##
DSW1]
conf t
int range f1/10 - 11
sw tr enc dot
sw mo tr
channel-group 1 mo on
exit
int range f1/14 - 15
sw tr enc dot
sw mo tr
channel-group 2 mo on
exit
int range f1/12 - 13
sw tr enc dot
sw mo tr
channel-group 4 mo on
end
wr
show ether summary
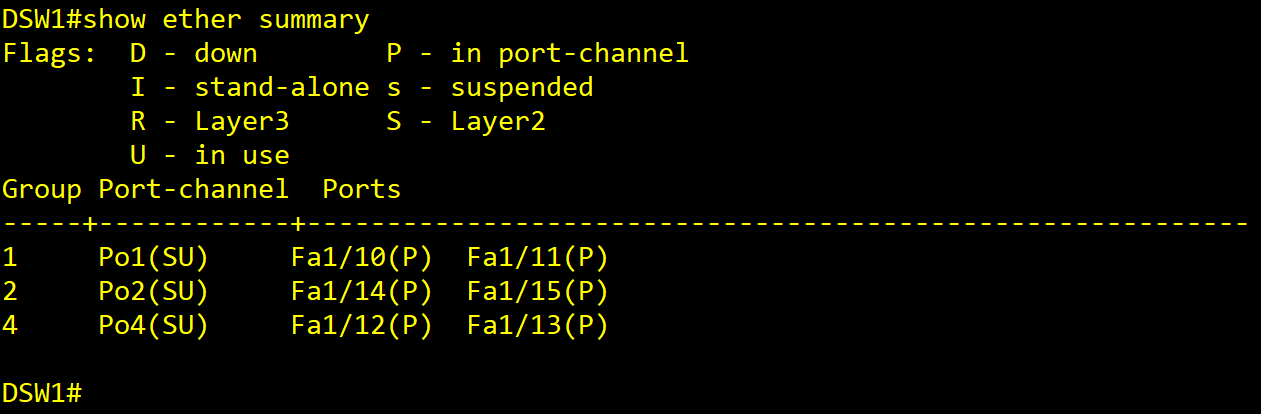
DSW2]
conf t
int range f1/10 - 11
sw tr enc dot
sw mo tr
channel-group 1 mo on
exit
int range f1/12 - 13
sw tr enc dot
sw mo tr
channel-group 3 mo on
exit
int range f1/14 - 15
sw tr enc dot
sw mo tr
channel-group 5 mo on
end
wr
show ether summary

ASW1]
conf t
int range f1/14 - 15
sw tr enc dot
sw mo tr
channel-group 2 mo on
exit
int range f1/12 - 13
sw tr enc dot
sw mo tr
channel-group 3 mo on
end
wr
show ether summary

ASW2]
conf t
int range f1/12 - 13
sw tr enc dot
sw mo tr
channel-group 4 mo on
exit
int range f1/14 - 15
sw tr enc dot
sw mo tr
channel-group 5 mo on
end
wr
show ether summary
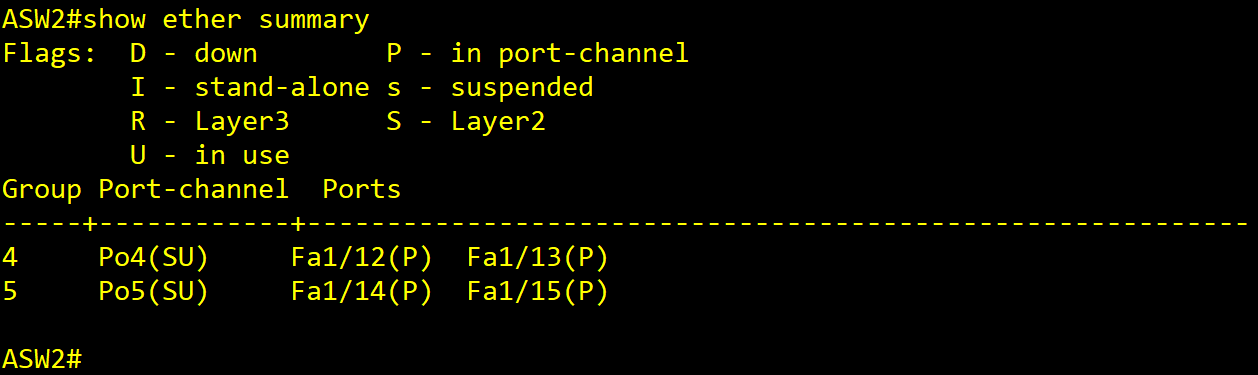

## Inside IP & OSPF ##
In_Router]
conf t
int f0/0
no shut
ip add 172.16.10.131 255.255.255.248
exit
int f0/1
no shut
ip add 172.16.10.139 255.255.255.248
exit
int f1/0
no shut
ip add 172.16.10.145 255.255.255.248
exit
int s2/0
int s2/0
no shut
encapsulation fram
no fram inver
clock rate 64000
ip add 211.230.60.1 255.255.255.252
fram map ip 211.230.60.2 102 br
exit
ip route 172.16.60.0 255.255.255.0 s2/0 211.230.60.2
ip route 0.0.0.0 0.0.0.0 f1/0 172.16.10.149
end
wr
DSW1]
## In_Router와 연결된 곳
conf t
int f1/1
no switchport
ip add 172.16.10.132 255.255.255.248
exit
int vlan 10
ip add 172.16.10.29 255.255.255.224
int vlan 20
ip add 172.16.10.61 255.255.255.224
int vlan 30
ip add 172.16.10.93 255.255.255.224
int vlan 40
ip add 172.16.10.125 255.255.255.224
end
wr
DSW2]
## In_Router와 연결된 곳
conf t
int f1/2
no switchport
ip add 172.16.10.140 255.255.255.248
exit
int vlan 10
ip add 172.16.10.30 255.255.255.224
int vlan 20
ip add 172.16.10.62 255.255.255.224
int vlan 30
ip add 172.16.10.94 255.255.255.224
int vlan 40
ip add 172.16.10.126 255.255.255.224
end
wr

SCR]
conf t
int s1/0
no shut
enc fram
no fram inver
clock rate 64000
ip add 211.230.60.2 255.255.255.252
fram map ip 211.230.60.1 201 br
## SCR에서 외부로 빠져나가는 곳이 CE밖에 없으므로 Default를 줘야 한다.
ip route 0.0.0.0 0.0.0.0 s1/0 211.230.60.1
int f0/0
no shut
ip add 172.16.60.254 255.255.255.0
end
wr

## 나머지 IP들 넣어주기. / ISP-NAT##
R4]
conf t
int vlan 70
ip add 2.2.2.254 255.255.255.0
exit
int f0/0
no shut
ip add 1.1.100.6 255.255.255.252
exit
ip route 0.0.0.0 0.0.0.0 f0/0 1.1.100.5
SCR]
conf t
int f0/1
no shut
ip add 211.230.60.2 255.255.255.252
exit
int f0/0
no shut
ip add 172.16.60.254 255.255.255.252
end
wr
ISP]
conf t
int f0/0
no shut
ip add 1.1.100.2 255.255.255.252
ip nat inside
exit
int f0/1
no shut
ip add 1.1.100.5 255.255.255.252
ip nat inside
exit
int f1/0
no shut
mac-address 06ff.0010.06e8
ip add dhcp
ip nat outside
exit
ip route 0.0.0.0 0.0.0.0 f1/0 10.0.0.1
ip route 2.2.2.0 255.255.255.0 f0/1 1.1.100.6
ip route 1.1.200.0 255.255.255.0 f0/0 1.1.100.1
## NAT
ip access-list standard DMZ_INSIDE
permit 1.1.100.0 0.0.0.3
permit 1.1.200.0 0.0.0.255
permit 2.2.2.0 0.0.0.255
exit
ip nat inside source list DMZ_INSIDE int f1/0 overload
end
wr
## OSPF ##
## 60.0 대역은 Static 으로 주기. 211 대역이 사설이라서 안된다.
In_Router]
conf t
int f0/0
ip os priority 100
exit
int f0/1
ip os priority 100
exit
router ospf 1
router-id 1.1.1.1
network 172.16.10.145 0.0.0.0 area 0
network 172.16.10.131 0.0.0.0 area 0
network 172.16.10.139 0.0.0.0 area 0
network 211.230.60.1 0.0.0.0 area 0
auto-cost reference-bandwidth 1000
redistribute static subnets
default-information originate always
end
wr
DSW1]
conf t
int vlan 10
bandwidth 200000
exit
int vlan 20
bandwidth 200000
exit
int vlan 30
bandwidth 200000
exit
int vlan 40
bandwidth 200000
exit
router ospf 1
router-id 2.2.2.2
network 172.16.10.29 0.0.0.0 area 0
network 172.16.10.61 0.0.0.0 area 0
network 172.16.10.93 0.0.0.0 area 0
network 172.16.10.125 0.0.0.0 area 0
network 172.16.10.132 0.0.0.0 area 0
auto-cost reference-bandwidth 1000
end
wr
DSW2]
conf t
int vlan 10
bandwidth 200000
exit
int vlan 20
bandwidth 200000
exit
int vlan 30
bandwidth 200000
exit
int vlan 40
bandwidth 200000
exit
router ospf 1
router-id 3.3.3.3
network 172.16.10.30 0.0.0.0 area 0
network 172.16.10.62 0.0.0.0 area 0
network 172.16.10.94 0.0.0.0 area 0
network 172.16.10.126 0.0.0.0 area 0
network 172.16.10.140 0.0.0.0 area 0
auto-cost reference-bandwidth 1000
end
wr
## HSRP ##
DSW1]
## 원래 ospf hello가 5초인데 10초로 변경해보자!
## 문제 생기면 우선순위값을 20을 깎아라. 그러면 얘가 standby가 된다.
conf t
int vlan 10
standby 10 ip 172.16.10.28
standby 10 priority 110
standby 10 preempt delay minimum 10
standby 10 track f1/1 20
exit
int vlan 20
standby 20 ip 172.16.10.60
standby 20 priority 110
standby 20 preempt delay minimum 10
standby 20 track f1/1 20
exit
int vlan 30
standby 30 ip 172.16.10.92
standby 30 preempt
exit
int vlan 40
standby 40 ip 172.16.10.124
standby 40 preempt
end
wr
DSW2]
## VLAN 10과 20은 Standby
conf t
int vlan 10
standby 10 ip 172.16.10.28
standby 10 preempt
exit
int vlan 20
standby 20 ip 172.16.10.60
standby 20 preempt
exit
int vlan 30
standby 30 ip 172.16.10.92
standby 30 priority 110
standby 30 preempt delay minimum 10
standby 30 track f1/2 20
exit
int vlan 40
standby 40 ip 172.16.10.124
standby 40 priority 110
standby 40 preempt delay minimum 10
standby 40 track f1/2 20
end
wr
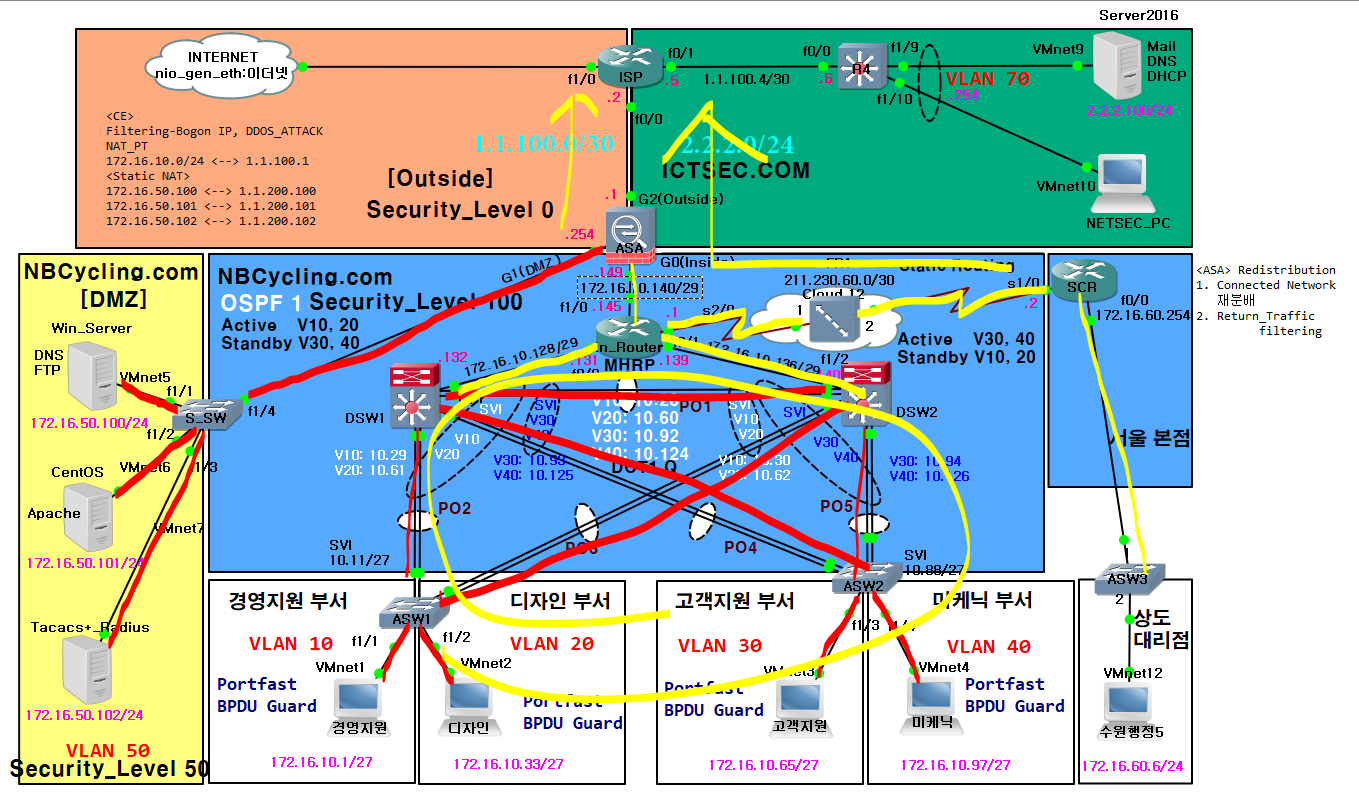
## ASA Interface 세팅 ##
ASA]
conf t
## Gigabit 0번 ## <Inside>
int g0
no shut
nameif Inside
security-level 100
desc ##Inside_Network##
ip add 172.16.10.149 255.255.255.248
exit
## Gigabit 1번 ## <DMZ>
int g1
no shut
nameif DMZ
security-level 50
desc ##DMZ_Network##
ip add 172.16.50.254 255.255.255.0
exit
## Gigabit 2번 ## <Outside>
int g2
no shut
nameif Outside
security-level 0
desc ##Outside_Network##
ip add 1.1.100.1 255.255.255.252
exit
show int ip br

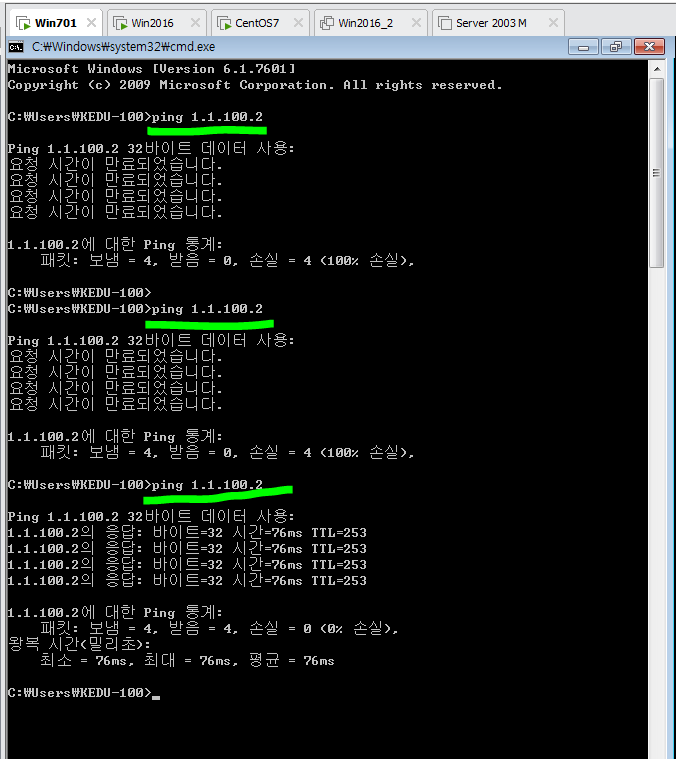
## 현재 Win701에서
ping 172.16.10.29 (O) - 게이트웨이 OK
ping 172.16.10.132 (O) - DSW1->In_Router
ping 172.16.10.131 (O) - In_Router->DSW1
ping 172.16.10.149 (O) - In_Router->ASA


## ASA Ping test 및 대역 알려주기 ##
## ASA에서의 Ping 허용 ##
ASA]
conf t
policy-map global_policy
class inspection_default
inspect icmp

## Static NAT ##
object network DNS_SVR
host 172.16.50.100
nat (DMZ,Outside) static 1.1.200.100
exit
object network WEB_FTP_SVR
host 172.16.50.101
nat (DMZ,Outside) static 1.1.200.101
exit
object network Inside
subnet 172.16.0.0 255.255.0.0
nat (Inside,Outside) static interface
## 172.16.0.0 /16 을 해줘야지 172.16.xxx.xxx을 모두 알게 된다.
route Inside 172.16.0.0 255.255.0.0 172.16.10.145
route Outside 0.0.0.0 0.0.0.0 1.1.100.1
## Object_Group ##
1. Object
특정 Network 혹은 Service를 Object로 정의하여 사용이 가능하며, Network와 Servcie object로 구분한다.
IP 대역을 'Network-Object'로 설정
| 172.16.10.0/24 | 본사 부서 (경영지원 / 디자인 / 고객지원 / 미케닉) |
| 172.16.60.0/24 | 상도 대리점 |
| 172.16.50.100 | DNS, FTP |
| 172.16.50.101 | Web, Mail |
ASA]
object network Headquarters
subnet 172.16.10.0 255.255.255.0
object network Agency
subnet 172.16.60.0 255.255.255.0
object network DNS_SVR
host 172.16.50.100
object network WEB_SVR
host 172.16.50.101
FTP, DNS Service Object를 설정.
object service DNS_P
service udp destination eq 53
object service FTP_P
service tcp destination eq 21
2. Object-Group
* 다수의 Network / Protocol / Service 등을 묶어서 하나의 Object-Group으로 정의할 수 있다.
또한 기존 Object / Object-Group을 포함하는 것도 가능하다.
## Inside (10, 60) 대역을 하나의 Network로 Group화 시키기.
| network-object 172.16.10.0/24 | 본사 |
| network-object 172.16.60.0/24 | 상도 대리점 |
ASA]
Object-Group network HQ_IN_NET
network-object object Headquarters
network-object object Agency

다음 조건에 맞도록 Service Object-Group를 설정하시오.
- Web Service : HTTP, HTTPs
- Mail Service : SMTP, POP3, IMAP
ASA]
Object-group service WEB_S
service-object tcp destination eq 80
service-object tcp destination eq 443
exit
Object-group service MAIL_S
service-object tcp destination eq 25
service-object tcp destination eq 110
service-object tcp destination eq 143
show run object-group

## Ping 용
access-list Admit_Ping_Test extended line 1 permit icmp 172.16.50.0 255.255.255.0 any
## ASA 6가지 정책 ##
| Inside -> Outside | 모든 접근 허용 |
| Inside -> DMZ | 53번 : DNS(UDP) - DNS_P 21번 : FTP(TCP) - FTP_P 80번 : HTTP(TCP) - WEB_S 443번 : HTTPS(TCP) - WEB_S 25번 : SMTP(TCP) - MAIL_S 143번 : IMAP(TCP) - MAIL_S |
| DMZ -> Inside | 모든 접근 차단 / Ping test용 ICMP만 허용 |
| DMZ -> Outside | 53번 : DNS(UDP) - DNS_P 21번 : FTP(TCP) - FTP_P 80번 : HTTP(TCP) - WEB_S 443번 : HTTPS(TCP) - WEB_S 25번 : SMTP(TCP) - MAIL_S 143번 : IMAP(TCP) - MAIL_S |
| Outside -> Inside | 모든 접근 차단 / Ping test용 ICMP만 허용 |
| Outside -> DMZ | 53번 : DNS(UDP) - DNS_P 21번 : FTP(TCP) - FTP_P 80번 : HTTP(TCP) - WEB_S 443번 : HTTPS(TCP) - WEB_S 25번 : SMTP(TCP) - MAIL_S 143번 : IMAP(TCP) - MAIL_S |
1. Inside -> Outside : 모든 권한 허용
ASA]
access-list INSIDE->DMZ permit ip any any
access-group INSIDE->OUTSIDE in interface Inside
access-list INSIDE->DMZ deny ip object-group HQ_IN_NET 172.16.50.0 255.255.255.0
## ???? 이거 deny인데 172.16.50.0 255.255.255.0
2. Inside -> DMZ : FTP, SMTP, DNS, HTTP, IMAP, HTTPS
ASA]
access-list INSIDE->DMZ extended permit object DNS_P object-group HQ_IN_NET object DNS_SVR
## HQ_IN_NET(Inside 대역 : 본사+대리점)에서 DNS_SVR(172.16.50.100)으로 갈 때,
DNS_P(53번:DNS)를 허락하라.
access-list INSIDE->DMZ extended permit object FTP_P object-group HQ_IN_NET object WEB_SVR
## HQ_IN_NET(Inside 대역 : 본사+대리점)에서 WEB_SVR(172.16.50.101)으로 갈 때,
FTP_P(21번:FTP)를 허락하라.
access-list INSIDE->DMZ extended permit object-group WEB_S object-group HQ_IN_NET object WEB_SVR
## HQ_IN_NET(Inside 대역 : 본사+대리점)에서 WEB_SVR(172.16.50.101)으로 갈 때,
WEB_S(80번:HTTP[www], 443번:HTTPS)를 허락하라.
access-list INSIDE->DMZ extended permit object-group MAIL_S object-group HQ_IN_NET object DNS_SVR
## HQ_IN_NET(Inside 대역 : 본사+대리점)에서 DNS_SVR(172.16.50.100)으로 갈 때,
MAIL_S(25번:SMTP, 143번:IMAP)를 허락하라.
access-list INSIDE->DMZ extended permit ip any any
## access-list INSIDE->DMZ deny ip object-group HQ_IN_NET 172.16.50.0 255.255.255.0 log 4 interval 60
access-group INSIDE->DMZ in interface Inside
4. DMZ -> Outside
ASA]
access-list DMZ->OUTSIDE extended permit icmp 172.16.50.0 255.255.255.0 any
access-list DMZ->OUTSIDE extended permit object DNS_P 172.16.50.100 255.255.255.255 any
access-list DMZ->OUTSIDE extended permit object FTP_P 172.16.50.101 255.255.255.255 any
access-list DMZ->OUTSIDE extended permit object-group WEB_S 172.16.50.0 255.255.255.0 any
access-list DMZ->OUTSIDE extended permit object-group MAIL_S 172.16.50.100 255.255.255.255 any
## access-list DMZ->OUTSIDE deny ip object-group HQ_IN_NET 172.16.50.0 255.255.255.0 log 4 interval 60
(일단 생략)
access-group DMZ->OUTSIDE in interface DMZ
6. Outside -> DMZ
ASA]
access-list OUTSIDE->DMZ extended permit icmp 2.2.2.0 255.255.255.0 any
access-list OUTSIDE->DMZ extended permit object DNS_P any object DNS_SVR
access-list OUTSIDE->DMZ extended permit object FTP_P any object WEB_SVR
access-list OUTSIDE->DMZ extended permit object-group WEB_S any object WEB_SVR
access-list OUTSIDE->DMZ extended permit object-group MAIL_S any object DNS_SVR
## access-list OUTSIDE_IN deny ip object-group HQ_IN_NET 172.16.50.0 255.255.255.0 log 4 interval 60
access-group OUTSIDE->DMZ in interface Outside
## PAT ##
object network Inside_NET
subnet 172.16.0.0 255.255.0.0
nat (Inside,Outside) dynamic interface
## 원래는 255.255.0.0 으로 해서 10+60 대역을 묶어주려 했는데, 대역을 좀 더 줄여서 깔끔하게 만드려고 192로 함.
## DNS Rewrite ##
object network DNS_RE
host 172.16.50.101
nat (DMZ,Outside) static 1.1.200.100 dns
인 터 넷 된 다 끼 야 호 인 터 넷 된 다 끼 야 호 인 터 넷 된 다 끼 야 호
인 터 넷 된 다 끼 야 호 인 터 넷 된 다 끼 야 호 인 터 넷 된 다 끼 야 호
인 터 넷 된 다 끼 야 호 인 터 넷 된 다 끼 야 호 인 터 넷 된 다 끼 야 호
인 터 넷 된 다 끼 야 호 인 터 넷 된 다 끼 야 호 인 터 넷 된 다 끼 야 호
## Apache Server 구축 ##
1. Apache
특정 Network 혹은 Service를 Object로 정의하여 사용이 가
'Network > Cisco (KEDU)' 카테고리의 다른 글
| 동적 라우팅 프로토콜 Test 2 (OSPF & EIGRP 재분배) (0) | 2021.11.08 |
|---|---|
| 동적 라우팅 프로토콜 Test 1 (OSPF) (0) | 2021.11.08 |
| P 리허설 (0) | 2021.07.26 |
| VLAN 이중화 Test (1시간 안에 풀어야 하는 과제, 배운거임.) (0) | 2021.07.12 |
| IPv4와 IPv6의 통신을 위한 터널링 기법 (0) | 2021.07.09 |




